End user cyber security policy (basic)
This policy covers some of the basics of cyber security. It is designed to help new and small businesses to develop their first end user cyber security policy. The clauses are mainly restrictive, stating what employees must and must not do.
This is intended to support people who have never attempted to write a policy before, so there are limited options to choose from. If you are looking for more flexibility or if you want to write a permissive policy (for instance, if you want a policy covering bring your own device or BYOD), see the standard and premium versions of this document.
This end user cyber security policy is the work of cyber security expert Emma Osborn of OCSRC Ltd (see https://www.ocsrc.co.uk/).
End user cyber security policy (basic) contents
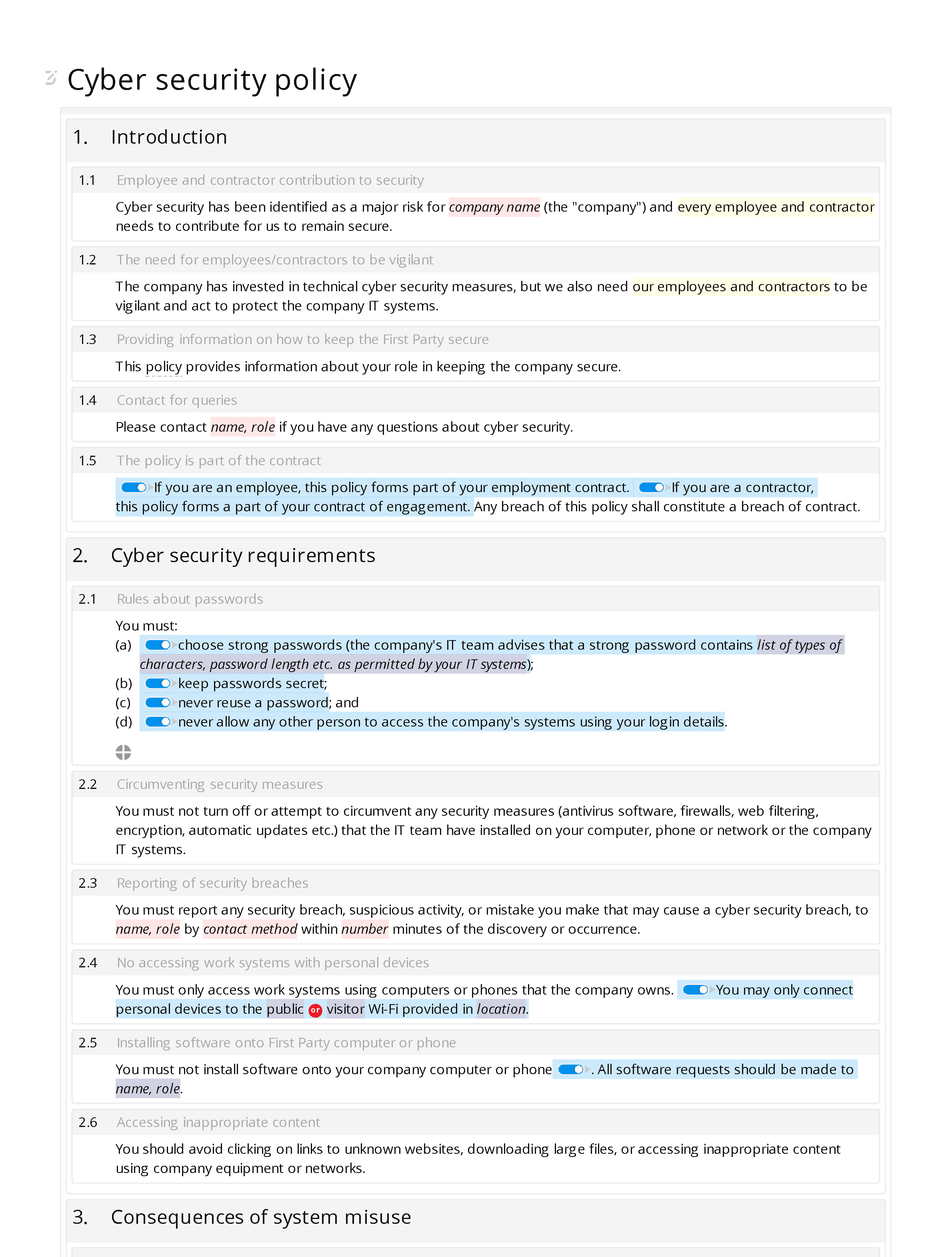
- Introduction: employee and contractor contribution to security; the need for employees/contractors to be vigilant; providing information on how to keep the companysecure; contact for queries ; the policy is part of the contract.
- Cyber security requirements: rules about passwords; circumventing security measures; reporting of security breaches; no accessing work systems with personal devices; installing software onto companycomputer or phone; accessing inappropriate content.
- Consequences of system misuse: actions considered to be misuse of IT systems; consequences of IT system misuse.
- Declaration: agreement to abide by policy; signature; signature line: first.
This is a shortened preview of the editor interface; once you create your instance you'll be able to edit the full document in our online editor.

This is a shortened preview of the DOCX output; once you create your instance you'll be able to download the full document in PDF, HTML, RTF and/or DOCX (Microsoft Word) format.


